Related News
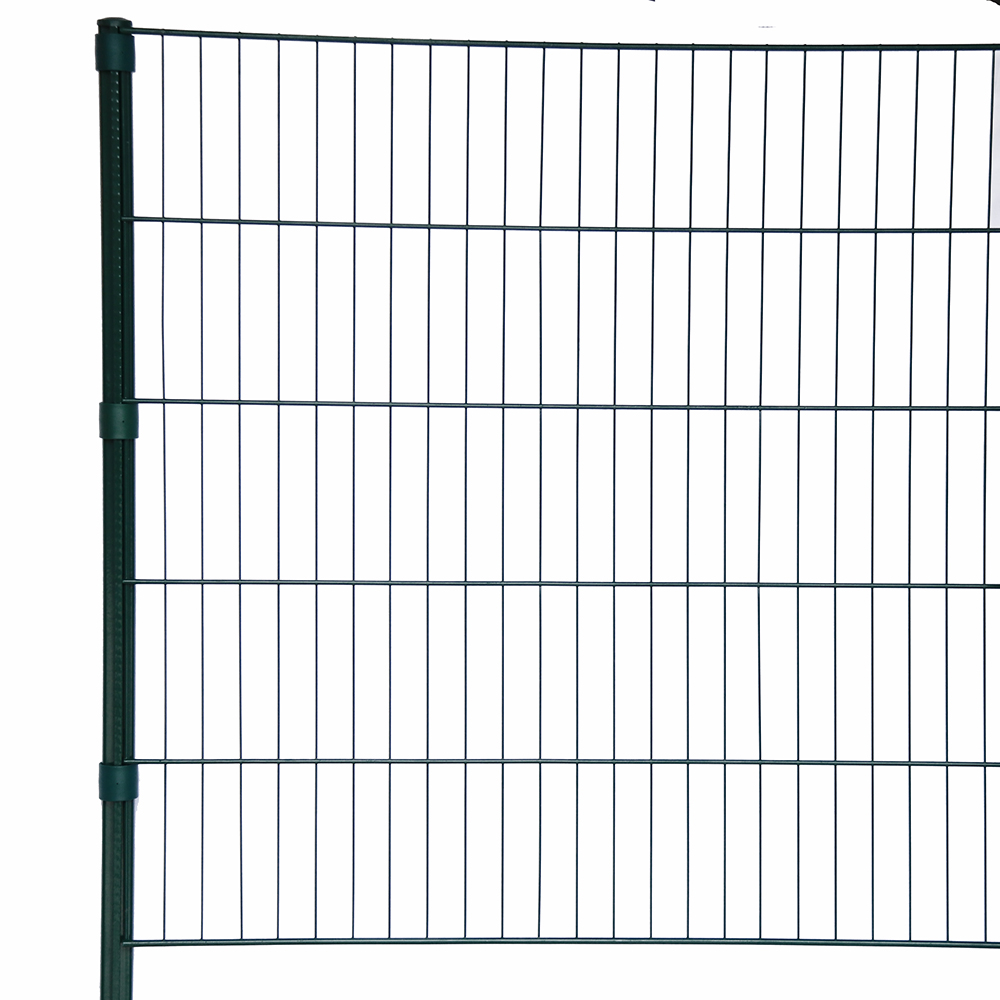
5 1 2 t post
Feb . 13, 2025 06:57In the fast-paced realm of technology, products emerging with innovative features often transform the way users engage with digital platforms. One term gaining traction in this evolving landscape is 5 1 2 T post. This keyword, albeit intriguing, requires an in-depth exploration to align with SEO optimization that emphasizes Experience, Expertise, Authoritativeness, and Trustworthiness.


Authoritativeness To establish authority, a product labeled with 5 1 2 T post should be backed by rigorous research and development, as well as endorsements from well-recognized figures in the tech industry. When prominent cybersecurity analysts or tech entrepreneurs confirm the credibility of the technology, it elevates the product’s status. Furthermore, collaborations with leading tech enterprises or institutions conducting groundbreaking research further solidifies authority. Documentation detailing the product's development process, security protocols, and case studies demonstrating successful implementation across various sectors contributes significantly to authoritative positioning in the market. Trustworthiness Trust is built through consistent performance and transparent communication with end-users. For a technology tagged with 5 1 2 T post, establishing trust involves clear user manuals, regular updates addressing possible vulnerabilities, and active customer support. A trustworthy product demonstrates accountability by responding swiftly to user feedback and incorporating constructive critiques into future iterations. Transparency in how data is handled and a user-centric privacy policy reinforce user confidence. Furthermore, robust testing phases, encompassing multiple environments to simulate potential misuse, corroborate the commitment to providing a secure and efficient product. In conclusion, while the term 5 1 2 T post may initially intrigue as an enigmatic keyword, its potential for product development is immense. By embracing the pillars of Experience, Expertise, Authoritativeness, and Trustworthiness, a product with this label can not only meet but exceed market expectations. This revolutionary approach to data handling can redefine user interaction with technology, fostering a digital ecosystem where speed, security, and reliability converge seamlessly.